

Updated · Jan 10, 2024
Updated · Oct 04, 2023
Raj Vardhman is a tech expert and the Chief Tech Strategist at TechJury.net, where he leads the rese... | See full bio
Girlie is an accomplished writer with an interest in technology and literature. With years of experi... | See full bio
A reverse proxy is a server that acts as a middleman between clients and web servers. Its primary duty is to manage incoming client requests and direct them to their corresponding backend servers.
The level of control provided by reverse proxies significantly enhances the overall website performance and security. In fact, more than 25 million currently operational websites use reverse proxies.
By the end of this article, you’ll learn the significance of a reverse proxy and how it operates. Delve deeper into this dynamic technology to unveil the factors contributing to its widespread usage among websites.
|
🔑 Key Takeaways
|
Smartproxy is a top-rated proxy provider trusted by many. Its 40 million+ proxies from 195+ locations help bypass CAPTCHAs, geo-blocks, and IP bans. It offers a free trial and has a high rating of 4.7 on Trustpilot with 89% 5-star ratings, making it one of the best in the industry.
Client-server communication is crucial in web applications. However, direct communication between clients and servers may pose some risks to data security for both parties.
Malicious users can attempt to exploit vulnerabilities in the server’s code or infrastructure, leading to security breaches. In 2022, the average total cost of a data breach reached a record-breaking amount of $4.35 million.
An intermediary layer between clients and servers offers a safe and regulated path for communication, making a reverse proxy a suitable choice for this task.
Every time a client sends a request to a website, the request is forwarded to the reverse proxy instead of going directly to the servers. Then, the reverse proxy will make its request to the appropriate server.

Having gained insight into how reverse proxy works, it’s time to explore their real-world applications. In the following segment, you’ll learn about the common uses of reverse proxies.
Handling requests on behalf of the servers is just one of the many uses of a reverse proxy. Its strategic positioning enables many benefits, from load balancing to facilitating A/B testing.
Discover each of them below:
One of the most important functions of a reverse proxy is load balancing. It ensures that the load is equally distributed among all servers to avoid overloading.

Reverse proxies use various algorithms in load balancing, such as:
By distributing client requests across multiple backend servers, load balancing improves overall system performance, scalability, and fault tolerance.
Caching is a technique used in computer systems to store and reuse frequently accessed data. It improves system performance by providing quicker access to data, as the stored or cached copy can be retrieved more rapidly.
Reverse proxies enhance caching efficiency by storing and delivering frequently requested resources directly to clients. This relieves backend servers and accelerates content delivery.

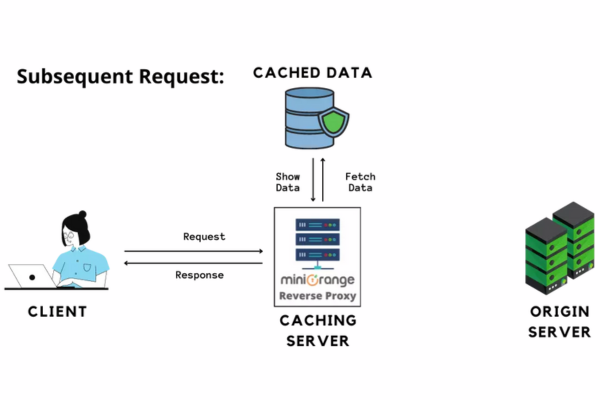
CDN extends the capabilities of caching even further. Reverse proxies can deliver content from edge servers closer to the clients, reducing latency.
Say a web server gets several requests from users all over the world. The requested asset is then pulled from that web server.
However, before returning the asset to the user, it is cached on the nearest edge server. If the same user asks for the same asset again, that edge server sends the response.

|
👍 Helpful Article: A CDN is necessary if you plan to increase your website’s speed. Check out this article to help you find the best CDN provider. |
Hackers typically perform malicious attacks by altering requests sent to a web server. However, an attacker cannot directly access the website's internal servers with a reverse proxy.
The reverse proxy can also identify the attacking user's IP address and deny them access to the server. As a result, it becomes more difficult for cybercriminals to launch an attack.
Here are some common web-based attacks that a reverse proxy server can prevent:
|
👍 Helpful Article: Cyberattacks are growing more sophisticated and complicated as time goes on. Find out what it is and how to deal with it in this article. |
Data transported over the Internet is encrypted using Transport Layer Security (TLS), an improved version of Secure Socket Layer (SSL). By doing this, you can prevent hackers from viewing your data.
This is especially helpful for the following:
As a result, every data that reaches the origin server is encrypted. However, encrypting and decrypting communications for each client can be expensive for an origin server. This is when a tool like reverse proxy comes in helpful.

SSL/TLS termination can be handled by reverse proxies, allowing them to offload backend servers' resource-intensive encryption and decryption procedure.
This approach increases overall system performance, particularly in cases with many secure connections.
|
💡 Did You Know? Business Email Compromise (BEC) incurred $43 billion in losses between 2016 and 2021. For many email users, this is a major worry. You can use SSL email protection to defend against cyberattacks. |
A/B testing, sometimes called split testing or bucket testing, analyzes two versions of a website or app’s landing page to evaluate which performs better.

A website or app screen is modified to produce a second version of the same page to do the test. Changes might range from a single headline or button to a complete website overhaul.
This helps companies determine which designs are most successful at turning site visitors into paying clients.
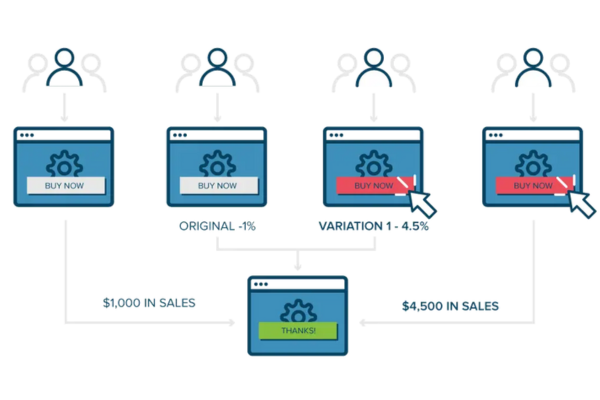
A reverse proxy is essential for supporting A/B testing since it statistically randomizes traffic to the various versions. The reverse proxy will continue employing the previously selected version whenever the user's browser makes future requests.
|
🎉Fun Fact: The design of a website plays a significant role, accounting for 75% of its overall credibility. Additionally, videos on landing pages can raise conversion rates by 86%. |
Reverse proxies offer a range of advantages that significantly enhance the performance, security, and web applications' scalability.
From load balancing to security features, reverse proxies provide a comprehensive solution for optimizing and protecting modern web architectures.
It can offer a range of advantages by leveraging the power of reverse proxies. Organizations can improve the user experience, achieve high availability, and ensure the smooth operation of their web applications.
A web application’s performance can be significantly improved by:
In addition to enhancing a website's efficiency, reverse proxies help decrease latency and network congestion.
|
⚠️Warning: Sensitive information may be stored in cache memory. To prevent unwanted access to your stored data, see our post on how to empty the Windows 10 and 11 caches. |
Regarding guiding website traffic, application layer routing encompasses the strategic determination of how data packets should be directed for intelligent traffic management. Reverse proxies excel in this area.
Requests can be routed to the most suitable backend server by employing reverse proxies, and the workload may be distributed more effectively.
Horizontal scalability, also known as scaling out, refers to the ability of a system to handle increased workload and demand by adding more servers.
However, achieving effective horizontal scalability may require designing the application architecture with distribution. Thankfully, reverse proxies can help meet these needs since it can distribute incoming traffic among multiple backend servers.
On top of that, reverse proxies ensure high availability configurations by providing failover mechanisms when a backend server becomes unavailable.
Reverse proxies may function as content filters by analyzing requests. They provide content constraints and rewriting capabilities, enabling clients and backend servers to exert precise control over the data flow.
This feature is useful in enforcing security policies and compliance requirements.
In certain cases, apps use the client's IP address for geolocation, analytics, and implementing access limits based on IP.
Fortunately, with a reverse proxy in place, a client's IP address is kept intact and sent to the backend servers.
|
📝Note: While IP address preservation may benefit corporations and marketers, it may cause concern for others. It's usually preferable if you can keep your IP address to yourself. |
One important security aspect is granular access control, which is finely managing user permissions in systems and apps. Reverse proxies simplify this by enforcing specific policies for protected resources.
This way, only those granted permission can access sensitive information or carry out certain tasks.
Verse proxies decrease bandwidth consumption by compressing content before delivering it to clients. This feature leads to faster page load times, lower bandwidth costs, and a better user experience.
|
💡Did You Know? By 2025, people are expected to generate 463 exabytes of data daily. To give you an idea, storing one exabyte would require between 10,000-100,000 personal computers. That’s a lot of data! |
There are many advantages to using reverse proxies. They do, however, have drawbacks that organizations should consider.
Understanding these drawbacks can aid organizations in making informed decisions when integrating reverse proxies into their systems.
The reverse proxy is an additional layer between the client and the server. Unfortunately, this process can introduce latency whenever a client requests data.
|
📙Definition: Latency is the time it takes for data to travel across a network. When network latency is too high, an application's performance suffers and may even crash. |
High latency can potentially slow down the overall response time of a website, affecting user experience.
Using a reverse proxy introduces a single point of failure in the infrastructure. If the reverse proxy server fails or becomes overloaded, it might disrupt the entire system, resulting in downtime and service interruptions.
Careful planning and configuration of failover systems is essential to mitigate this risk.
Organizations with several diverse backend servers may find it extremely challenging to set up and configure a reverse proxy.

Proper configuration requires a thorough understanding of the proxy server software and the backend applications it interacts with.
It’s important to note that inadequate configuration can result in routing errors, security vulnerabilities, and performance issues.
Handling SSL certificates for multiple domains and subdomains can be challenging using a reverse proxy.
Managing and renewing SSL certificates for each domain can become cumbersome, particularly in large-scale deployments.
At the same time, improper management of SSL certificates can lead to security vulnerabilities and may affect the availability of a website’s services.
As mentioned earlier, reverse proxies incorporate caching mechanisms to improve performance. However, caching dynamic or personalized content can be problematic.
Deleting and updating the cache can be challenging for websites with dynamic content, which is constantly updated or tailored to the user.


Processing time is increased when a proxy is used because of the need to manage requests, connections, and other proxy-specific, resulting in performance-related challenges such as:
Businesses should carefully assess the impact on performance and ensure the selected reverse proxy solution can handle the anticipated demand.
Some reverse proxy servers only handle a few protocols, which limits the range of applications or services they can efficiently administer.
Choose a reverse proxy solution that aligns with the specific requirements of the backend applications.
The additional degree of abstraction introduced by a reverse proxy can make troubleshooting difficult.
Organizations must consider this and should be willing to invest time and resources in troubleshooting before employing a reverse proxy.
Certain web pages or technologies that require specific prerequisites may cause reverse proxies to fail. To ensure compatibility, assess the proxy's capabilities through detailed testing.
Implementing a reverse proxy solution often involves relying on a specific vendor or software. This dependency can limit flexibility and vendor lock-in.
Organizations should carefully evaluate the long-term viability and support of the chosen reverse proxy solution to avoid potential issues in the future.
Leveraging IP monitoring and data encryption, reverse proxies can potentially retain sensitive data like passwords. This can be problematic if it’s run by a malicious party, considering that every 39 seconds, a hacking incident takes place.
In addition, since this information is extremely sensitive, they are responsible for maintaining the following:

Here is a rundown of the upsides and downsides of using a reverse proxy:
|
Advantages |
Disadvantages |
|
Improved Performance |
Increased Latency |
|
Application Layer Routing |
Single Point Of Failure |
|
Scalability and High Availability |
Configuration Complexity |
|
Content Filtering |
SSL Certificate Challenges |
|
IP Address Preservation |
Caching Challenges |
|
Granular Access Control |
Performance Overhead |
|
Bandwidth Optimization |
Limited Protocol Support |
|
Debugging and Troubleshooting |
|
|
Compatibility Issues |
|
|
Vendor Dependency |
|
|
Threat Posed by Data Storage |
|
👍 Helpful Article: Now that you've learned all there is to know about reverse proxies. Find out how to set up your reverse proxy with the help of this in-depth article. |
A reverse proxy is a vital component of modern web infrastructure, offering numerous benefits such as load balancing, security, content caching, and SSL termination.
By intelligently managing incoming requests and distributing them to backend servers, reverse proxies optimize website delivery and ensure a seamless user experience.
Understanding reverse proxies' capabilities and use cases of reverse proxies can empower businesses to make informed decisions when optimizing their web applications.
On the contrary, a virtual private network (VPN) conceals its users' identities, while a reverse proxy conceals those of web servers.
In contrast to a reverse proxy, which sits between a client and a server, a forward proxy sits between a client and an external network, such as the Internet.
No. Instead, a reverse proxy may serve as an API gateway. API gateways provide a wider range of functions than reverse proxies, particularly regarding API maintenance.
While reverse proxies may improve security by serving as a barrier between clients and backend servers, they can also become a target for attackers if not properly configured or maintained.
Your email address will not be published.
Updated · Jan 10, 2024
Updated · Jan 09, 2024
Updated · Jan 05, 2024
Updated · Jan 03, 2024





